A security vendor has discovered a huge list of easily searchable stolen credentials in cleartext on the dark web which it fears could lead to a new wave of cyber attacks.
Julio Casal, co-founder of identity threat intelligence provider 4iQ, which has offices in Calfornia and Spain, said in a Dec. 8 blog his firm found the database of 1.4 billion username and password pairs while scanning the dark web for stolen, leaked or lost data.
He said the company has verified at least a group of credentials are legitimate.
What is alarming is the file is what he calls “an aggregated, interactive database that allows for fast (one second response) searches and new breach imports.” For example, searching for “admin,” “administrator” and “root” returned 226,631 passwords of admin users in a few seconds. As a result, the database can help attackers automate account hijacking or account takeover.
Casal says the file is almost two times larger than the previous largest credential exposure, the Exploit.in combo list that exposed 797 million records. It is not entirely new data, but an aggregation of 252 previously breaches, including known credential lists such as Anti Public and Exploit.in, decrypted passwords of known breaches like LinkedIn as well as smaller breaches like Bitcoin and Pastebin sites. However, it does include information from 133 new breaches. “We’ve found that although the majority of these breaches are known within the Breach and Hacker community, 14 per cent of exposed username/passwords pairs had not previously been decrypted by the community and are now available in clear text,” said Casal.
Among other things the database shows how some people still re-use passwords on many sites. For example, one person may have thought they were being safe by using an uncommon 10 digit password –but used it on six email addresses.
4iQ also used the database to generate a list of top common passwords. They include the usual suspects:
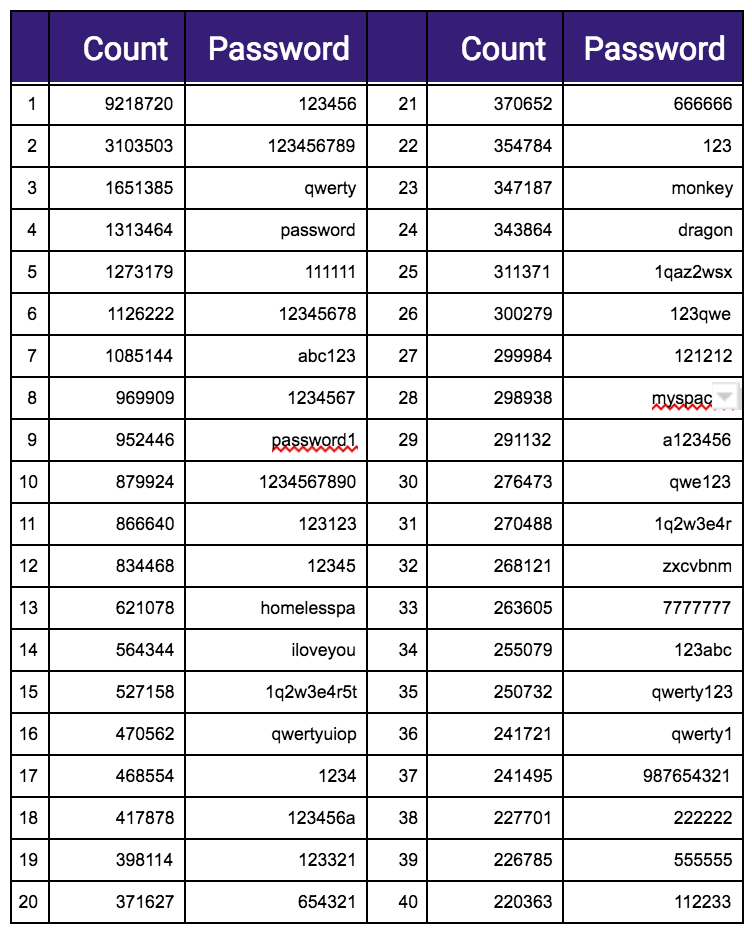
There is no indication who created the database and tools, but whoever it was included Bitcoin and Dogecoin wallets for any user who wants to make a donation.
In a column this morning SecurityWeek contributor Kevin Townsend quotes several experts worrying about how the database could be used. One said an attacker could just pick a target company and search for references to it in the list to find staff, contractors or suppliers. “This could give both an initial foothold into the company, or — if someone is already in — to help move around if credentials have been reused internally.”
