The recent crippling of four computers by ransomware at the Ottawa Hospital is another reminder that awareness training can’t be an annual event.
The hospital confirmed over the weekend that over a three-week period four people clicked on email that contained the malware which froze their devices.
“What the hospital IT department did was wipe the drives and restored it from a backup…No ransom was paid out,” Kate Eggins, the institution’s director of media relations, said in an interview. She also emphasized that no patient data was affected.
Fortunately the malware wasn’t sophisticated enough to search the network and duplicate itself. Officials have concluded it wasn’t a targeted attack, she added.
The hosptial’s IT director is away this week for March break and wasn’t available to answer questions about the type of attachment and why staff fell for it, awareness training and why endpoint protection didn’t stop the Trojan.
Eggins said the ransomware was WinPlock, a variant of CryptoLocker.
Endpoint security vendors have given it various names. ESET, for example, calls it Win32/Filecoder, and says it dates back to at least April, 2015. Typically it uses the The RC4 encryption algorithm and demands payment in Bitcoin to unlock a PC.
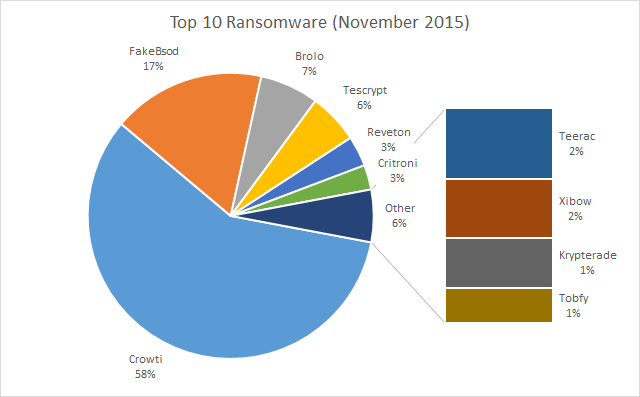
Graphic from Microsoft
Marc-Etienne Leveille, a Montreal based malware researcher at ESET said in an interview that email attachments are increasingly the way ransomware is being delivered — sometimes targeted, sometimes randomly.
“They are very clever emails that look legitimate, like invoices. Those campaigns are quite successful, unfortunately. We’ve also seen ransomware distributed via exploit kits with traffic being redirected to an exploit kit server and running the ransomware if the operating system and browser is not up to date.”
For example, over the weekend it was discovered that hackers had taken over a Web advertising network to install malicious ads on MSN, bbc.com, the New York Times, AOL and Newsweek. The ads linked to an updated version of the Angler exploit kit, which includes ransomware.
In addition to regular awareness training, Leveille said CISOs have to ensure there is layered security and offline backup of important data. That’s particularly necessary because ransomware can lock up not only the local drive but also attached network and USB storage.
Ted Harrington, executive partner at Baltimore-based Independent Security Evaluators, a security assessments consulting firm added this advice:
“Organizations need to build a threat model — what trying to protect; who is trying attack you, what are their characteristics; and what are your attack surfaces against which an adversary will launch their campaign to compromise your assets. For an org to go through that process and its important to have availability of that critical data, it needs to be built into their defence methodology. So if the threat model is properly built and properly effectively articulates the assets, adversaries and attack surfaces that are relevant, they’ll be able to put in place defence mechanisms that are effective against those types of attacks.”
Coincidentally this week cloud services provider Intermedia released a survey of 275 IT experts at third party vendors such as managed service providers, IT consultants and resellers who were asked about their customers experience with ransomware.
It provided some insight into the controversy of whether to pay up. Forty-three per cent said their customers have been victims of the malware. Of them, 18 per cent paid the ransom. But of those that paid 19 per cent didn’t get their systems restored by the attacker.
Ransomware has increased so much in the past few years that the U.S. Institute for Critical Infrastructure Technology — supported by a number of vendors including BlackBerry and Hewlett-Packard Enterprise — said in a report this month that “2016 is the year ransomware will wreak havoc on America’s critical infrastructure community,” which includes hospitals.
Last month, the report notes, attackers encrypted the email system and patient records of Hollywood Presbyterian Hospital in Los Angeles and demanded a ransom of US$17,000 in Bitcoins. After almost two weeks, the hospital paid.
