You’d hope that a mechanism for troubleshooting problems of operating system isn’t an opening for a cyber attack. However, that’s exactly was has happened to Windows Troubleshooting Platform (WTP).
According to security vendor Proofpoint, attackers have found a way to leverage WTP to socially engineer email recipients into executing malware by an attachment.
“This attack is particularly effective since execution of WTP is not accompanied by a security warning and users have been conditioned to run the troubleshooter when it appears in Windows,” the company said in a blog. “In this case, though, running the troubleshooter leads to the installation of LatentBot, a well-documented modular bot used for surveillance, information stealing, and remote access.”
When the user opens the file, they are asked to “double-click to auto detect charset.” In the case presented, to the user the opened file seems to be gibberish, but in fact it opens an embedded OLE object, a digitally signed DIAGCAB file, which is the Windows extension for a Troubleshooting pack. When the pack is opened, the user sees a dialogue box that says “Troubleshoot and help prevent computer problems.” If the user clicks on “Next,” the application launches a PowerShell command to download and launch the payload.
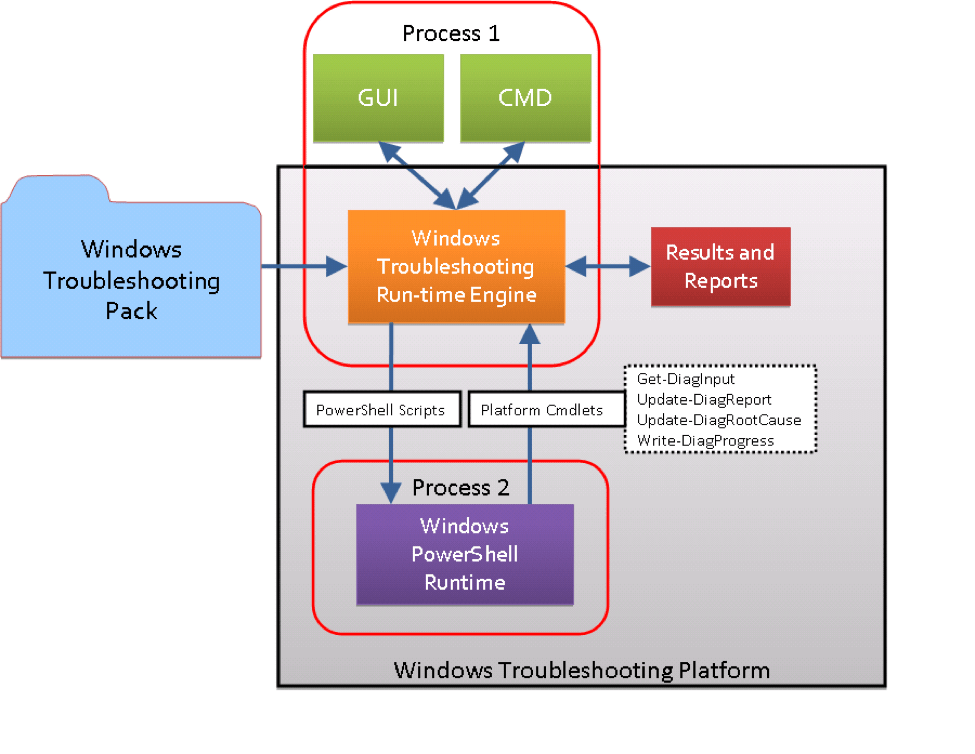
While the troubleshooting dialogue box lists a publisher to give authenticity, that firm is uninvolved. A valid certificate was compromised and used to deliver the attack.
“This method of malware execution bypasses observation by many existing sandbox products because the malicious activity is carried out outside of the msdt.exe binary loading the .diagcab file,” notes Proofpoint. “This continues the trend of malware authors seeking new sandbox evasion methods via COM-based non-standard execution flow.”
According to FireEye, Latentbot only keeps malicious code in memory for the short time that is needed. Most of the encoded data is found either in the program resources or in the registry, the company says. A custom encryption algorithm is shared across the different components, including in encrypting its command and control (CnC) communications. Due to this, its family binaries are detected with a generic name such as Trojan.Generic:
At this point the only defence is security awareness training.
