By now most CISOs know that criminals as well as corporations are leveraging software-as-a-service. This week Check Point Software released a report looking at how the Nuclear exploit kit, which it says was one of the world’s largest attack infrastructures until it shut down recently amid exposure by security researchers at Check Point and Cisco Systems.
Cisco estimated attackers using Nuclear have been successfully targeting and compromising users in more than 10,000 different cities in more than 150 countries including Canada. Check Point last month Nuclear attacked close to 1,85 million machines around the world, with almost 10 per cent of them being infected.
As the Check Point report explains, Nuclear is rented to cybercriminals for a few thousand dollars a month. Researchers discovered it had 15 active control panels (so 15 attackers could be using it at a time) suggesting organizers — suspected to be in Russia — could have been pulling in US$100,000 a month.
From the panel the subscriber can chose the malware wanted for an attack. The overwhelming majority were ransomware — often the Locky dropper — followed by banking Trojans. While Nuclear often changes exploits to evade detection, favoured platforms are Flash, JavaScript and VBscript vulnerabilities.
In operation the service provider owns the master server, which controls the 15 attacker servers. Each attacker receives his own Nuclear control panel, where the campaign can be viewed and managed. Each server has a number of landing page servers. Unsuspecting users are directed to these compromised Website servers to be infected.
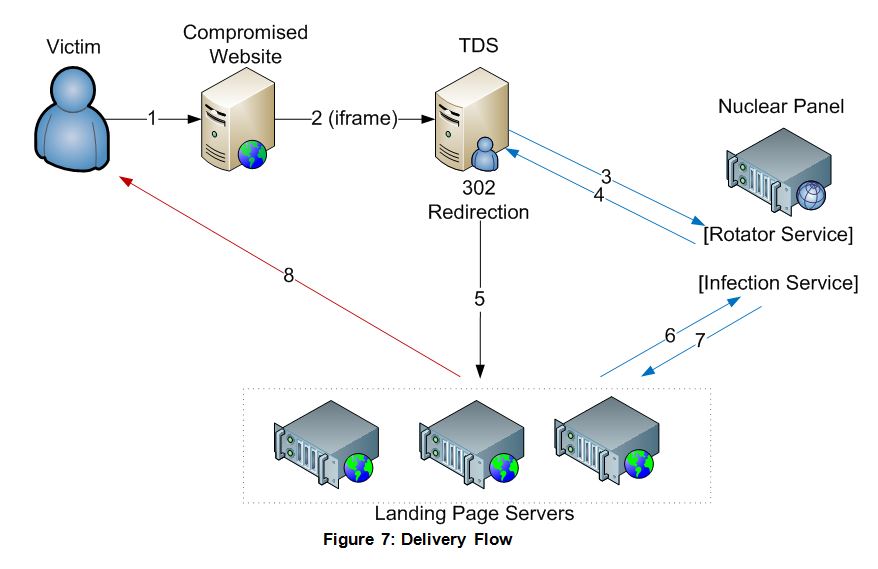
These reports again underscore the importance to CISOs of either eliminating Flash from their environments or ensuring users’ computers have to click to approve a Flash download. In addition, patching for other exploits — like JavaScript and VBScript — has to be timely.
Internet service providers also have to take notice, because often they are unwitting hosts to malware as a service. Cisco researchers complied a list of around a dozen IPs that were hosting the Nuclear exploit kit. One of them helped with the take down on its servers and with data showing how the kit operates.
