A server with databases holding the phone numbers and identity numbers of perhaps as many as 200 million Facebook users in the U.S., the U.K. and other countries has been found open on the Internet by a security researcher.
No one knows who the database belongs to, how or when it was copied from Facebook, according to TechCrunch, which first reported the discovery Wednesday.
A total of 413 million records are in the databases, but according to news reports, roughly half of them are duplicates.
TechCrunch quoted Facebook spokesperson Jay Nancarrow as saying the data had been scraped before Facebook cut off public access to user phone numbers over a year ago. Until then users could search the social media site for phone numbers.
“This data set is old and appears to have information obtained before we made changes last year to remove people’s ability to find others using their phone numbers,” Nancarrow said. “The data set has been taken down and we have seen no evidence that Facebook accounts were compromised.”
However, TechCrunch noted that in the hands of a threat actors a phone number could be used at least for spam calls, and at worst for SIM-swapping attacks, where a cell carrier is tricked switching the phone number of a user to another device.
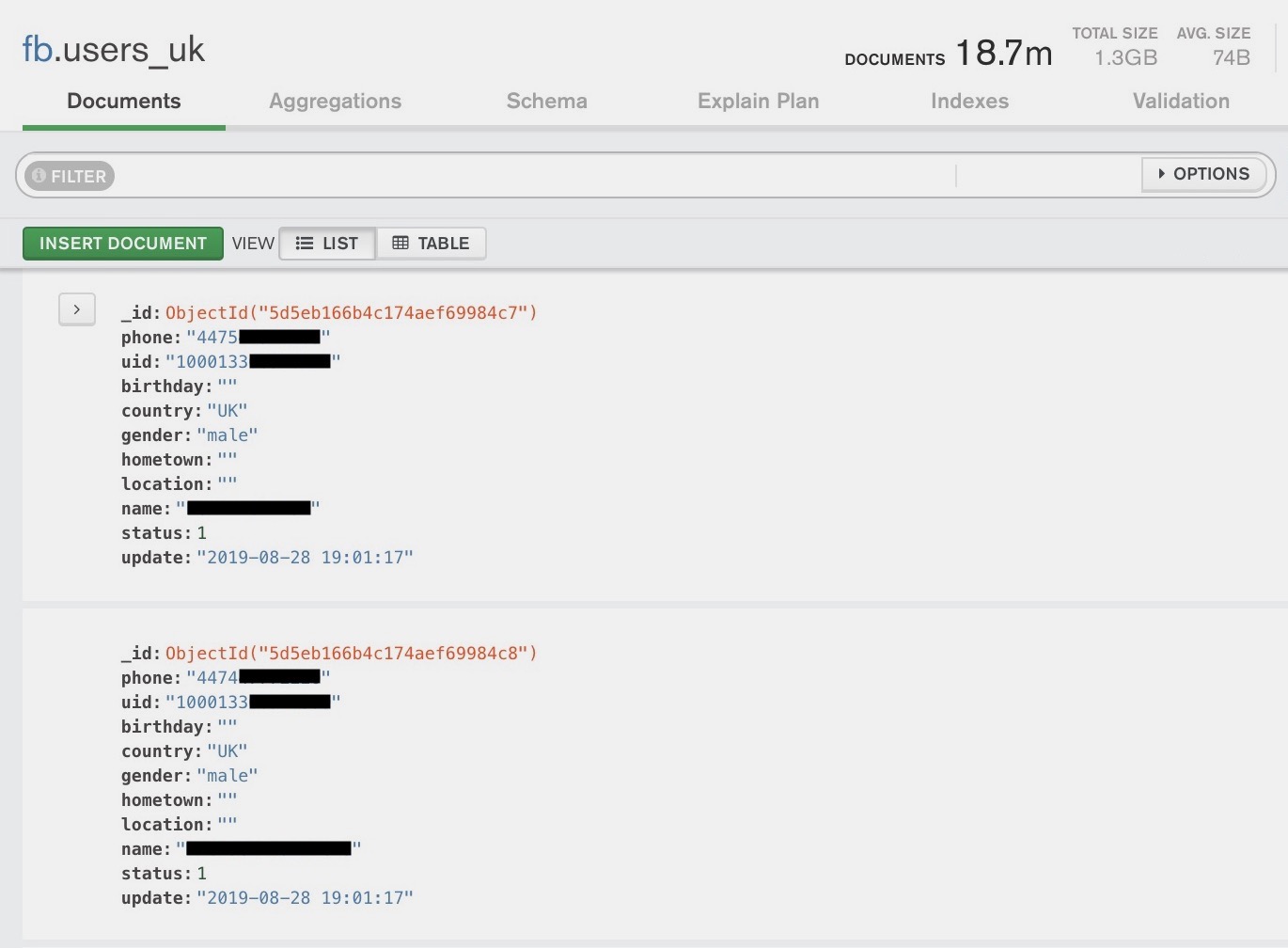
Each record in the databases contained a user’s unique Facebook ID and the phone number listed on the account. A user’s Facebook ID is typically a long, unique and public number associated with their account. TechCrunch said it can easily be used to discern an account’s username. Some of the records also had the user’s name, gender and location by country.
TechCruch said this is a typical page found in the database:
Sanyam Jain, a security researcher and member of the GDI Foundation, found the database and contacted TechCrunch after he was unable to find the owner. The news site also couldn’t find the owner but was able to identify the web host, who pulled the server offline.
Ashlee Benge, a threat researcher at security vendor ZeroFox, noted that when phone numbers associated with identities are leaked, like in this case where they are associated with specific Facebook profiles, it poses a high risk for SIM swapping attacks. These kinds of attacks occur when either a phone number or associated account is hijacked. This information is especially valuable to account takeover forums that specialize in these attacks. Whether these attacks are conducted to take over an account and drain associated bank accounts or bitcoin wallets, or as a publicity stunt, it’s important to protect yourself against these types of cybercriminals.
To better secure accounts and prevent these kinds of attacks, she recommends enabling the option to be notified when a login occurs from a new device. Additionally, although it will not prevent account hijacking if a phone number has been taken over, we also recommend that two-factor authentication be enabled whenever possible. This is best done with an app like Google Authenticator or Duo. If SMS-based two-factor authentication is required, we recommend using Google Voice.
