The Conti ransomware gang will strike fast, deep and persistently into an organization with hands-on attacks, including delivering the ransomware payload into memory, according to a detailed analysis released Tuesday.
It comes from Sophos, which looked into an attack against a customer that ran over four days, although on the second day nothing happened after the initial penetration
The first in a series of three reports was released today.
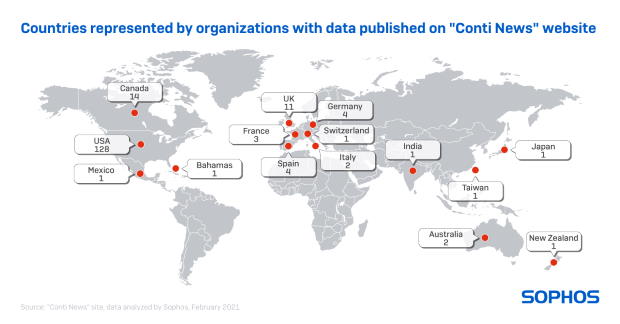
Conti is a “double extortion” gang that steals and threatens to expose information as well as encrypting it. The Conti News site has published stolen data from at least 180 victims to date, including 128 organizations in the U.S. and 14 in Canada.
In the Sophos case study, the unnamed victim organization’s weak point was a Fortinet FortiGate firewall running vulnerable firmware. Once inside, the attacker gained domain admin access to two servers simultaneously. This took the attacker 16 minutes.
Over the next six hours, the attacker deployed a Cobalt Strike beacon, a tool to communicate with a command and control server and gather network intelligence. While the organization was able to shut down that attack, it didn’t realize the attacker had access to another server.
It took 15 minutes for the attacker to pivot to the second server, deploy another Cobalt Strike beacon and continue the attack, which included gathering a list of endpoints and servers to build a map of the victim’s network. A domain admin account on a third server was gained, which soon also added a Cobalt Strike beacon to continue this work.
Apparently, nothing happened the next day. But on day three, the attacker identified directories with potentially valuable data and began copying and exfiltrating files from the HR, IT, credit and accounting departments, as well as files from senior staff, to an account on Mega’s cloud storage platform. The attacker also searched for user credentials, copying all XLSX files with the string “pass” in the filename.
The horrors of day four
On day four, Cobalt Strike loaders were installed on nearly 300 endpoints and servers. Forty minutes later, the Conti ransomware was released using a technique called reflective DLL injection. With it, the ransomware code could run in memory and start encrypting each machine. Sophos says its anti-malware was able to block the ransomware on PCs and servers it was installed on, but not unprotected devices.
Once the victim’s IT department realized what was going on it shut down its critical infrastructure. In this case, the company was able to restore data from backups and restart most of its infrastructure less than 24 hours later.
“Because the reflective loaders deliver the ransomware payload into memory, never writing the ransomware binary to the infected computer’s file system, the attackers eliminate a critical Achilles’ heel that affects most other ransomware families,” one of the reports notes. “There is no artifact of the ransomware left behind for even a diligent malware analyst to discover and study.”
Peter Mackenzie, manager of Sophos Rapid Response team, described the attacks as “very fast” and “potentially devastating.”
“In attacks where humans are at the controls, adversaries can adapt and react to changing situations in real-time,” he said in a statement. “In this case, the attackers had simultaneously gained access to two servers, so when the target detected and disabled one of these – and believed they’d stopped the attack in time – the attackers simply switched and continued their attack using the second server. Having a ‘Plan B’ is a common approach for human-led attacks and a reminder that just because some suspicious activity on the network has stopped, it doesn’t mean the attack is over.”
Sophos says every organization has to use layered security to prevent cyberattacks. Similarly, to effectively react to any cyberattack the organization has to have an effective incident response plan that is regularly tested and updated.
Plus, Sophos provided the following advice to infosec leaders who are hit or suspect they are being hit by any variant of ransomware:
- Watch for early indicators an attacker is present. These include evidence of a network scanner, especially on servers; evidence of unauthorized tools for disabling antivirus; the presence of Mimikatz tool for saving credentials; patterns of suspicious repetitive behaviour; evidence of test attacks.
-
If you are certain there’s been an infection shut down internet-facing remote desktop protocol (RDP) to deny cybercriminals access to networks.
-
If you need access to RDP, put it behind a VPN connection.
- Assume attackers have compromised email so don’t use normal channels of communication to talk to people.
. - Only shut down devices if you can disconnect the network.
