Microsoft is taking a step towards blocking malware-bearing macros, one of the biggest tools used by threat actors to spread malware through phishing.
The company said today that the running of Visual Basic macros will be blocked by default in five Office applications, starting in April.
“While we provided a notification bar to warn users about these macros, users could still decide to enable the macros by clicking a button,” Kellie Eickmeyer, a member of Microsoft’s Tech Community, said in a blog. “Bad actors send macros in Office files to end users who unknowingly enable them, malicious payloads are delivered, and the impact can be severe, including malware, compromised identity, data loss, and remote access.”
“For the protection of our customers, we need to make it more difficult to enable macros in files obtained from the internet.”
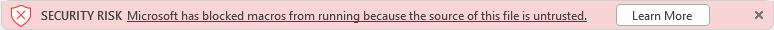
After the change, once a user opens an attachment or downloads an Office file containing macros from the internet, they will no longer be able to enable content with a click of a button. Instead, a message bar will display a Security Risk alert that the file contains Visual Basic for Applications (VBA) macros obtained from an untrusted source, and provides a Learn More button to click.
“The default is more secure and is expected to keep more users safe, including home users and information workers in managed organizations,” Eickmeyer said.
Macro-based malware continues its rise, Microsoft’s security team noted in a separate blog. Recent data from the Office 365 Advanced Threat Protection service indicates 98 per cent of Office-targeted threats use macros.
“The enduring appeal for macro-based malware appears to rely on a victim’s likelihood to enable macros,” Microsoft said.
- allows an enterprise to selectively scope macro use to a set of trusted workflows;
- blocks easy access to enable macros in scenarios considered high risk;
- provides end-users with a different and stricter notification so it is easier for them to distinguish a high-risk situation against a normal workflow.
This feature can be controlled via Group Policy and configured per application. It enables enterprise administrators to block macros from running in Word, Excel, and PowerPoint documents that come from the Internet. This includes scenarios such as the following:
- documents attached to emails that have been sent from outside the organization (where the organization uses the Outlook client and Exchange servers for email);
- documents opened from public shares hosted on the Internet (such as files downloaded from file-sharing sites);
- documents downloaded from Internet websites or consumer storage providers (like OneDrive, Google Drive, and Dropbox). However, a macro will not be blocked when the file is opened from the OneDrive location of the user signed into the client, i.e., your own OneDrive location, or when the file is opened from within the tenant (OneDrive for Business or SharePoint Online) of the user signed into the client, i.e., your own tenant.
This change only affects Office on devices running Windows, and only affects the following applications: Access, Excel, PowerPoint, Visio, and Word. The change will begin rolling out in Version 2203, starting with Current Channel (Preview) in early April 2022. Later, the change will be available in the other update channels, such as Current Channel, Monthly Enterprise Channel, and Semi-Annual Enterprise Channel.
At a future date to be determined, Microsoft also plans to make this change to Office LTSC, Office 2021, Office 2019, Office 2016, and Office 2013.